Large political bot network supporting Awami League on facebook revealed by Dismislab

A recent investigation by Dismislab, an independent information verification organization based in Dhaka, has revealed a sophisticated political bot network on Facebook.
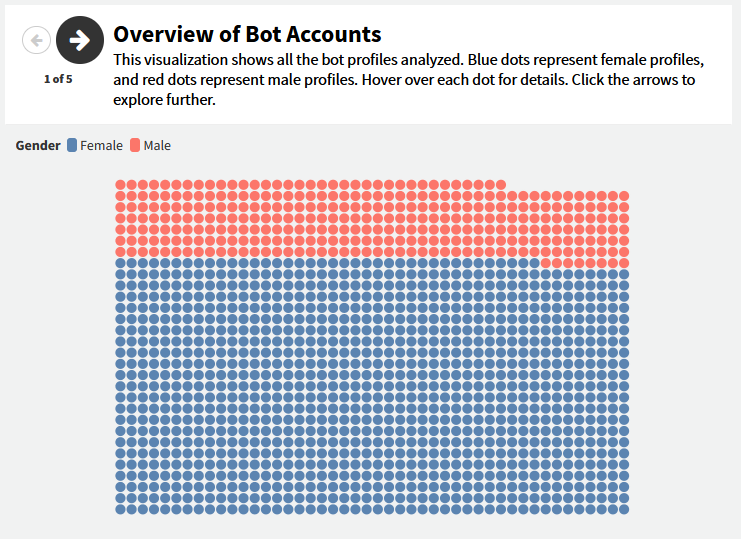
This network, involving 1,369 fake accounts, has been responsible for posting over 21,000 coordinated comments supporting Bangladesh’s former ruling party, Awami League.
The network, which was active around the 12th parliamentary election, persisted in its activities well beyond the election's conclusion.
The investigation was sparked by a June 21 article from the online news outlet bdnews24.com, titled “Is there an invisible code on every page printed by a color printer?”
The technical nature of the story might not have caught the attention of political enthusiasts, but it intrigued a researcher from Dismislab—not because of the article itself, but due to a comment made on the Facebook post:
“This election will be transparent. People will be able to vote freely in the upcoming election. The BNP is scared to participate because they can’t rig the vote this time.”
The researcher was surprised by the subsequent comments. Even months after the election, users continued to make remarks criticizing the opposition party and its leaders, expressing hopes for a fair election, and insisting on the election being held under the current government.
This doubt led Dismislab to uncover a bot network consisting of 1,369 Facebook accounts, which was responsible for over 21,000 coordinated comments in support of the then-ruling party, Bangladesh Awami League, across various Facebook pages.
The network became active just before the 12th Parliamentary Election and continued its activities afterward, focusing particularly on pages linked to established media outlets and the opposition, especially the Bangladesh Nationalist Party (BNP).
How did Dismislab find out about the bot network?
The investigation started by examining every comment on the bdnews24.com post, expanding to 196 other posts with similar comments and creating a 35,000-comment database.
Over 21,000 were linked to bot accounts, originating from 474 unique comments repeatedly posted. The final dataset focused on comments posted more than 10 times. The actual scale of the operation might be larger.
The bots mainly targeted political posts, but sometimes made errors, particularly with Bangla terms coincidentally containing letters transliterated as "EC".
This led to comments on unrelated posts like the one about color printers, where "IC" in "MIC" was misread as "EC". The final database revealed the political keywords and comments used by the network.
Analysis revealed that most accounts associated with the network shared typical traits of political bots: they were locked or private, created pre-election, had missing or stolen profile pictures, few or no friends, and followed only two specific pages.
Meta defines Coordinated Inauthentic Behavior (CIB) as coordinated actions, often using fake accounts, to manipulate public discourse for strategic purposes.
The bot network's actions seem largely automated, selecting posts based on keywords and posting pre-written comments, with minimal human intervention.
Dr. Naeemul Hassan, an Assistant Professor at the University of Maryland, acknowledged that Dismislab's findings indicate the use of computational tools but emphasized the importance of recognizing the analysis's limitations.
While the repetitive and coordinated nature of the comments suggests automation, Dr Naeemul pointed out that the investigation lacks direct evidence, such as a detailed examination of bot behavior or insights into specific algorithms.
Unearthing a profile pattern
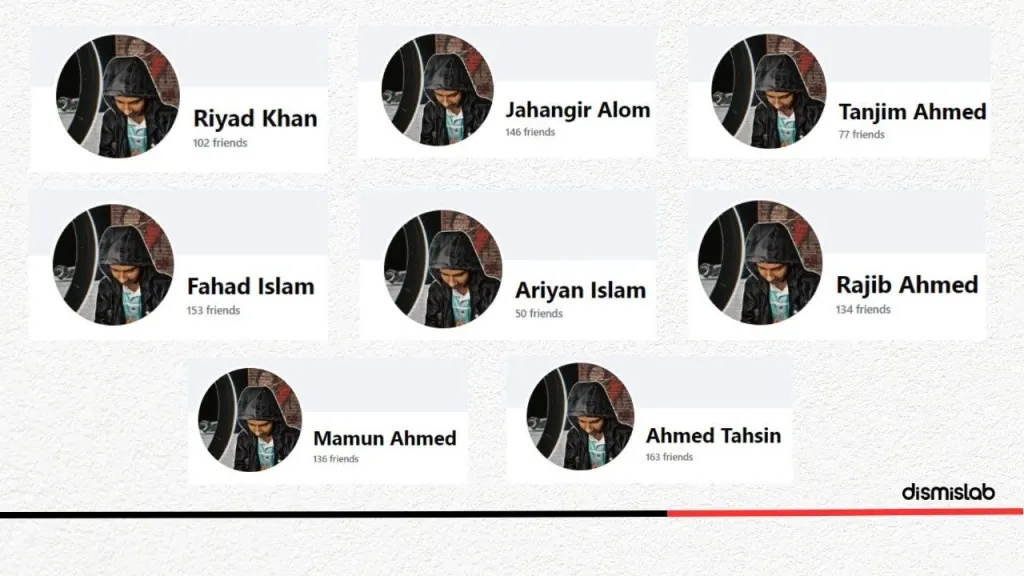
Dismislab's research revealed 1,369 accounts, with 77% being female profiles exhibiting striking similarities. For instance, 24% of these had the last name "Akter" with variations like Diya Akter, Riya Akter, etc.
Male profiles often used "Ahmed" or "Islam" and 90% of names, regardless of gender, were two words, sometimes splitting single names like Ri Pa or Li Za.
Exoperts and cybersecurity firms suggest identifying fake Facebook profiles by looking for restricted privacy, minimal "About" information, unusual posting patterns, internet-sourced profile pictures, and low friend counts.
Dismislab's analysis of the 1,369 accounts revealed that 247 profiles were locked. Among the remaining accounts, 70% used profile pictures found online, with some pictures being reused by multiple accounts.
For instance, one unique picture was used by eight different accounts on the same day. Similar patterns were seen with 19 other pictures, shared among 111 accounts. Female-named accounts also exhibited this picture-sharing behavior.
These findings further support the suspicion that these profiles are fake and part of a coordinated network.
As McAfee notes, fake accounts often use attractive images to gain attention, a trend seen in this network too, with pictures of Bangladeshi and South Indian actresses being used.
Among the unlocked profiles, 85% lacked "About" information, and 93% had no public posts besides profile and cover photos. Nearly half didn't display friend counts, and 45% had under 200 friends. Only seven accounts posted regularly, often sharing similar content.
Linked bot network and coordinated activities
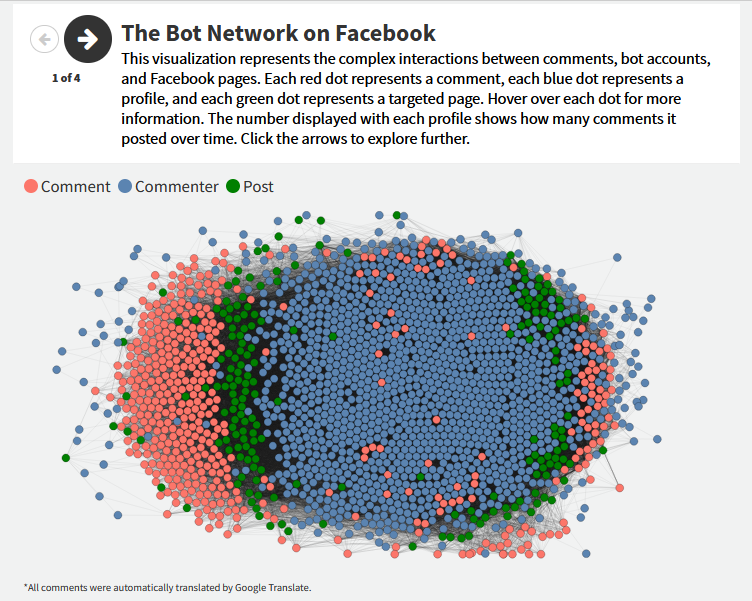
This research identified a total of 21,221 political comments, but only 474 of these were unique. The bots repeatedly circulated these 474 comments across different posts.
The analysis reveals a clear interconnection among the bots, as shown in the visualization below. For example, a profile named Riya Akter posted 138 comments across various posts over the past six months.
On May 18, well after the election, one of her comments was: “Bangladesh is an independent, sovereign country. An independent Election Commission (EC) has been formed here by law. The upcoming national election will be neutral, I hope.” This comment appeared on 96 posts by 109 bot accounts, including Diya Akter, Raisa, Rafia Akter, Nahid, and Nipa.
Another frequently used comment was: “Only those who have no faith in the people are afraid. That’s why BNP is scared to participate in the election,” which appeared 244 times.
This comment was posted by 217 bot profiles across various posts. On a sports news post on Channel i’s Facebook page, eight people, including Arian Munna, Nusrat Faria, and Ratna Akter, used the same comment.
Evidence suggests numerous bot accounts posted the same comments with identical spelling errors. Similar mistakes were found in a Chinese CIB network in 2022.
Additionally, 70% of active profiles followed the same two specific pages, further indicating their interconnectedness.
Timing analysis reveals 88% of comments were posted within two hours, with 151 bot comments appearing in 1 hour and 40 minutes on a single news link.
It is to be noted that Meta has taken action against CIB in Bangladesh, removing accounts before the 2018 election and again in 2024.
Whom did the bot target and what went wrong for them?
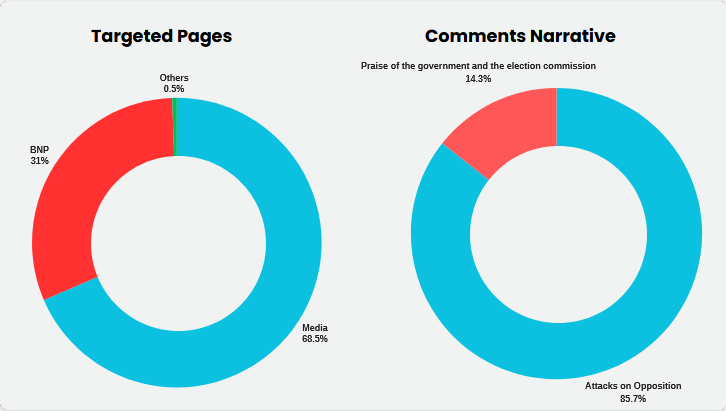
The bot network mainly targeted media outlets and Awami League's political opponents, with 68% of targeted pages being major media outlets and 31% linked to the BNP.
Content analysis shows 86% of bot comments criticized or attacked the BNP, while the remaining 14% supported the government and Election Commission, advocating for peaceful and fair elections.
Of the news articles receiving comments, 36% were related to the BNP, while the remaining articles covered topics such as Upazila elections, the National Parliamentary Election, and the Election Commission.
The bot network targeted posts with key terms like BNP, Election Commission, and Sheikh Hasina, ensuring coordinated comments on news items featuring these keywords.
Despite the 12th National Parliamentary Election being held on January 7, bot comments continued to refer to “the upcoming 12th National Parliamentary Election” through February to June.
For example, the comment “The upcoming 12th National Election must be free, fair, and participatory...” appeared 123 times across 49 posts after January 7, showing a lack of human oversight in the posting process.
The bots frequently made politically charged comments on irrelevant news stories. For example, they criticized the opposition or supported the government on posts about a bank robbery, a former president's death, a cricket venue change, or an actress's hospitalization.
These comments often appeared under posts containing Bangla words with letter sequences that resembled "EC" (Election Commission) when transliterated. This suggests that the bots relied on keyword-based computational tools to select posts for their political commentary.
In 2022, Meta identified a Russian CIB network exhibiting similar bot-comment behavior under unrelated posts. Additionally, the 2024 Adversarial Threat Report for the first quarter noted a comparable Israeli network.
Dr. Naeemul Hassan from the University of Maryland views the bot network revealed by Dismislab as a case of computational propaganda.
After reviewing the study’s findings independently, he remarked, “These activities primarily involve the use of advanced technology, driven by the coordinated efforts of both humans and computational tools.”
____

